 Earlier this month I attended the European Identity Conference in Munich. The conference is put together by Kuppinger Cole + Partner and they do a great job. As I’ve posted before each year it gets better, and this year was no exception. This year there were great sessions with cutting edge content, really good food and beer, and vibrant interaction between vendors and customers. It all added up to a very productive week. Oh, and there was really good beer.
Earlier this month I attended the European Identity Conference in Munich. The conference is put together by Kuppinger Cole + Partner and they do a great job. As I’ve posted before each year it gets better, and this year was no exception. This year there were great sessions with cutting edge content, really good food and beer, and vibrant interaction between vendors and customers. It all added up to a very productive week. Oh, and there was really good beer.
Last year, Martin Kuppinger and I led a workshop on cloud computing, and we did it again this year much more in depth – but that’s another post. This year, there was a whole content track devoted to the cloud. As I see it, cloud computing has evolved to become just “the cloud†and is a set of technologies and business models which have the requisite force to drive adoption of identity-based security. So combining an identity conference with a cloud conference is a Very Good Idea.
I gave a keynote in the Cloud 2010 track. KCP were kind enough to post the video of the session . You can also download the presentation. One advantage of my occasionally-derided “Wall of Words†presentation style is that you can easily get the main points by scanning through the presentation. I took all the photos in the presentation in Munich a few days before the session, which made it more relevant and fun for me.
The concepts in the presentation have emerged in the last year while working on Novell’s Cloud Security Service . Supporting insights and statistics came from a survey initiated by our own Anita Moorthy. Basically the presentation covers how business drivers affect the security needs of enterprises, SaaS vendors and cloud providers.
A survey of some current market forces and players:
- We have seen many times how a disruptive force in information systems is departmental autonomy pulling in products and services under the enterprise IT radar. This is again a significant factor in the adoption of SaaS applications.
- The adoption of SaaS applications is accelerating a shift by traditional hosting companies and telcos to IaaS and PaaS models, and they are increasingly moving to attract SaaS vendors in addition to enterprises.
The business and security interactions in the cloud involve enterprises, SaaS vendors, and cloud providers – each with different motivations. From this current cloudscape, I identified 3 trends and possible traps in each:
- Identity-based security is increasing in importance. Cloud services are pushing enterprises to emphasize identity based security rather than network security
- SaaS and IaaS are converging on PaaS. Infrastructure providers are moving up stack and applications need to be extensible… converging on platform services, including identity services.
- Cloud providers are increasingly offering identity services – and becoming identity providers. Identity services provide much needed security, and stickiness. Application marketplaces are a powerful paradigm growing around identity provider hubs.
We concluded with some recommendations for enterprises, SaaS vendors and cloud providers.
 For years, we have been working on standardizing, implementing, and deploying the identity provider model – which separates the sources of authentication and identity information from services that use identity information. It is clearly a better model for humans than separate accounts in every service. However, as Jeff Bohren succinctly said, “Change is hard. Passwords are easy.†More than ever I see trends in cloud computing that are finally providing the business model and incentives for enterprises, SaaS vendors, and cloud providers to move to the identity provider model. EIC 2010 further accelerated those trends.
For years, we have been working on standardizing, implementing, and deploying the identity provider model – which separates the sources of authentication and identity information from services that use identity information. It is clearly a better model for humans than separate accounts in every service. However, as Jeff Bohren succinctly said, “Change is hard. Passwords are easy.†More than ever I see trends in cloud computing that are finally providing the business model and incentives for enterprises, SaaS vendors, and cloud providers to move to the identity provider model. EIC 2010 further accelerated those trends.
I very much enjoyed the conference, working with the KCP team, and the interaction with customers, competitors and partners.
As always, I’d appreciate any feedback on the presentation, offers of presentation rewriting, coaching on public speaking, etc.





 When
When  What this means is that users of OpenSUSE 11.1 can install and run DigitalMe as easily as Firefox or Open Office or any other package. Just open up the package manager, search for digitalme and install. There are actually two packages that start with digitalme. One is the identity selector itself and the other is the Firefox addon. If you install the digitalme-firefox package, the selector is installed automatically. And you are automatically notified of updates!
What this means is that users of OpenSUSE 11.1 can install and run DigitalMe as easily as Firefox or Open Office or any other package. Just open up the package manager, search for digitalme and install. There are actually two packages that start with digitalme. One is the identity selector itself and the other is the Firefox addon. If you install the digitalme-firefox package, the selector is installed automatically. And you are automatically notified of updates!
 The
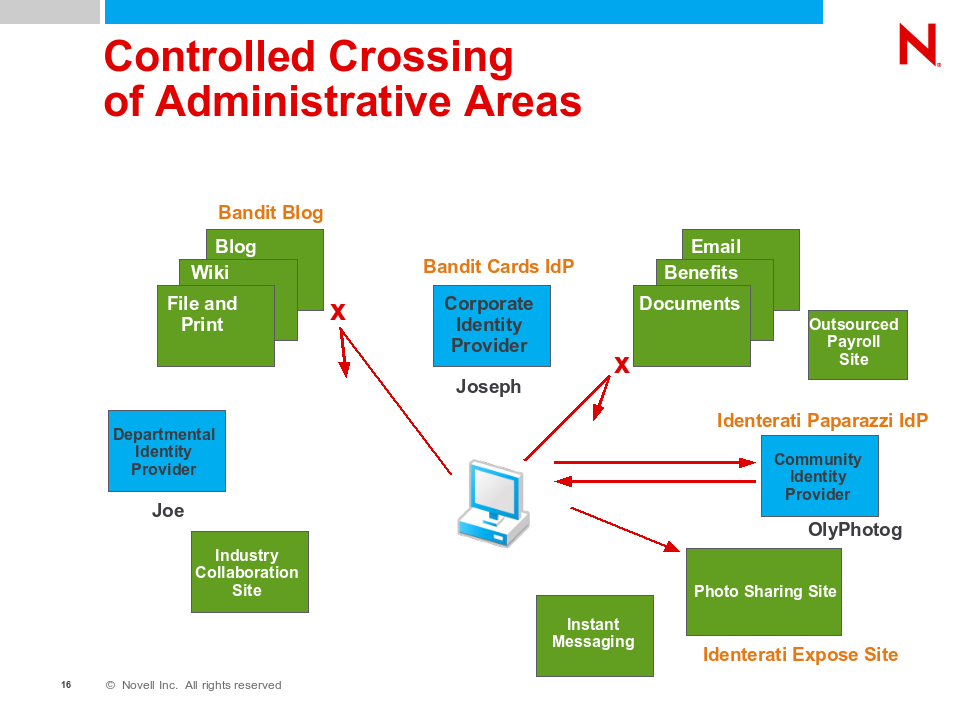
The  For example, managed information cards can be issued in auditing or non-auditing mode. In auditing mode, the identity provider knows who the relying party is and can control if and what data is securely sent to the Relying Party. In non-auditing (or privacy) mode the identity provider does not know where the data is to be sent — and hence cannot audit or change what data is sent based on that knowledge.
For example, managed information cards can be issued in auditing or non-auditing mode. In auditing mode, the identity provider knows who the relying party is and can control if and what data is securely sent to the Relying Party. In non-auditing (or privacy) mode the identity provider does not know where the data is to be sent — and hence cannot audit or change what data is sent based on that knowledge.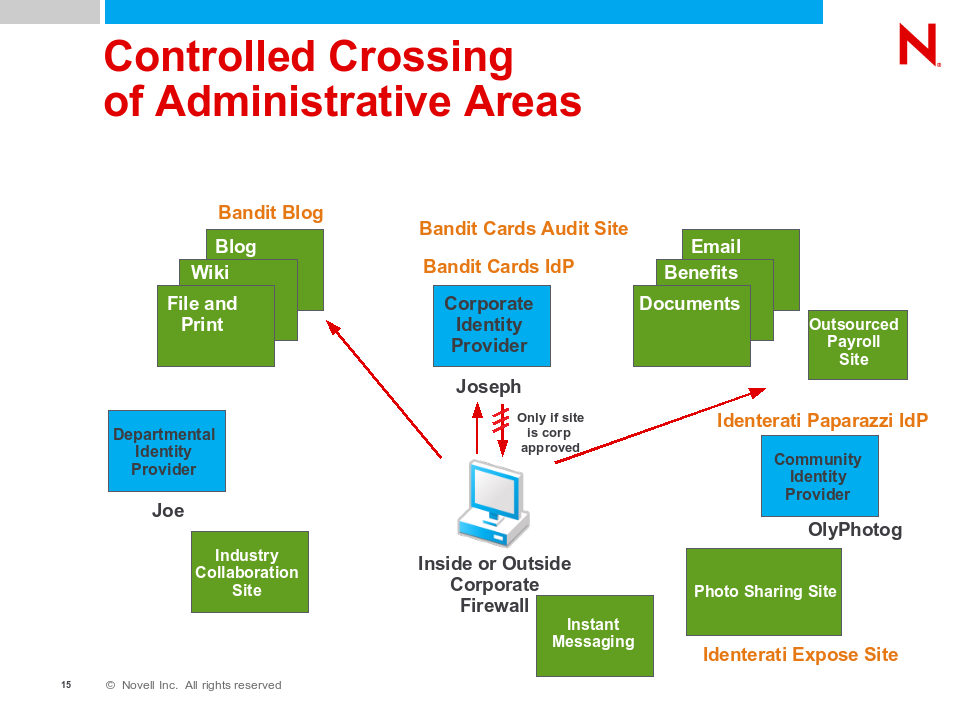
 Along those lines, at Novell’s Brainshare conference there was a panel discussion about “Open Source and User-centric Identity in the Enterprise”. The discussion was moderated by Carolyn Ford, and included Kim Cameron, Pamela Dingle, Patrick Harding, and myself. A
Along those lines, at Novell’s Brainshare conference there was a panel discussion about “Open Source and User-centric Identity in the Enterprise”. The discussion was moderated by Carolyn Ford, and included Kim Cameron, Pamela Dingle, Patrick Harding, and myself. A  For example, information card systems allow for assertions of identity data to be securely transmitted from an authoritative source to a network service in such a way that the user cannot tamper or see the data, yet is a control point for the release of the data.
For example, information card systems allow for assertions of identity data to be securely transmitted from an authoritative source to a network service in such a way that the user cannot tamper or see the data, yet is a control point for the release of the data. All of these perspectives are useful, and they are all useful within the enterprise, outside of the enterprise, and especially when crossing such boundaries.
All of these perspectives are useful, and they are all useful within the enterprise, outside of the enterprise, and especially when crossing such boundaries.