 The OSIS working group of the Identity Commons is completing their third interop. In OSIS-speak, an interop is a set of features and a time period where many projects and vendors test with others’ components to ensure that user-centric identity systems actually work together. Interops have always been concluded with one or more public demonstrations of the progress. It’s been greatly expanded this time with many more participants and test cases. We had demos for 2 days at the RSA conference, and will be showing more at the European Identity Conference in Munich next week.One part of this interop that I think is most significant is that we have are testing some features that are particularly useful in enterprise identity management scenarios. In my sessions and in discussing the OSIS interop at RSA, I found that many people were not aware of some of these capabilities.
The OSIS working group of the Identity Commons is completing their third interop. In OSIS-speak, an interop is a set of features and a time period where many projects and vendors test with others’ components to ensure that user-centric identity systems actually work together. Interops have always been concluded with one or more public demonstrations of the progress. It’s been greatly expanded this time with many more participants and test cases. We had demos for 2 days at the RSA conference, and will be showing more at the European Identity Conference in Munich next week.One part of this interop that I think is most significant is that we have are testing some features that are particularly useful in enterprise identity management scenarios. In my sessions and in discussing the OSIS interop at RSA, I found that many people were not aware of some of these capabilities.
 For example, managed information cards can be issued in auditing or non-auditing mode. In auditing mode, the identity provider knows who the relying party is and can control if and what data is securely sent to the Relying Party. In non-auditing (or privacy) mode the identity provider does not know where the data is to be sent — and hence cannot audit or change what data is sent based on that knowledge.
For example, managed information cards can be issued in auditing or non-auditing mode. In auditing mode, the identity provider knows who the relying party is and can control if and what data is securely sent to the Relying Party. In non-auditing (or privacy) mode the identity provider does not know where the data is to be sent — and hence cannot audit or change what data is sent based on that knowledge.
The capabilities of auditing and non-auditing cards exactly fit with some enterprise use cases I have experienced. It’s almost like they were designed with those use cases in mind. In fact, I remember hearing Kim Cameron and Mike Jones describe these modes at the very first Internet Identity Workshop in 2005, for just such use cases. Now it’s great to see them implemented and working — and it’s very cool to see it first in 100% open source implementations.
To see how auditing information cards could be used in an enterprise scenario, the Bandit project put together a live demo for Brainshare. It’s still operational and we continue to use these sites for OSIS testing. Check out the demo overview, instructions and links for more detail.
The quick overview of sites and services:
- We added to our existing Bandit Cards identity provider the ability for users to be issued auditing and non-auditing cards.
- We deployed a community identity provider
- Various other sites that illustrate how identity information can be appropriately used and managed.
More information about Bandit Employee Cards, and Bandit Member cards from the demo information page about the Bandit Cards IdP:
This is an instance of the Bandit Identity Provider. It is the repository of user account information, and (for purposes of this demo) represents a corporate identity source. It issues a number of types of information cards:
- An Employee Card. This card could be used to access information that should only be used in corporate approved sites, therefore Employee cards are issued in auditing mode. All uses of the card (each time a token is retrieved) are audited and the destination site for the token is recorded. If the card is attempted to be used at an unapproved site, no token is issued.
- A Member Card. This card is not used to access sensitive corporate identity data, it can be used to get member discounts at various sites. It essentially conveys a token which states that the bearer is an member.
Another site is the Bandit Blog. The intent is that only holders of Bandit Employee Cards should be able to post to the blog.
We also instantiated an identity provider service that is intended to represent a community site, The Identity Paparazzi. It issues non-auditing cards to it’s members. They like to post photos to a hypothetically contentious photo sharing site called “Identerati Exposé“.
Hence, in our twisted little hypothetical minds we could see some scenarios.
(Note: use “view image†to see more detail in the following diagrams, and the photos above)
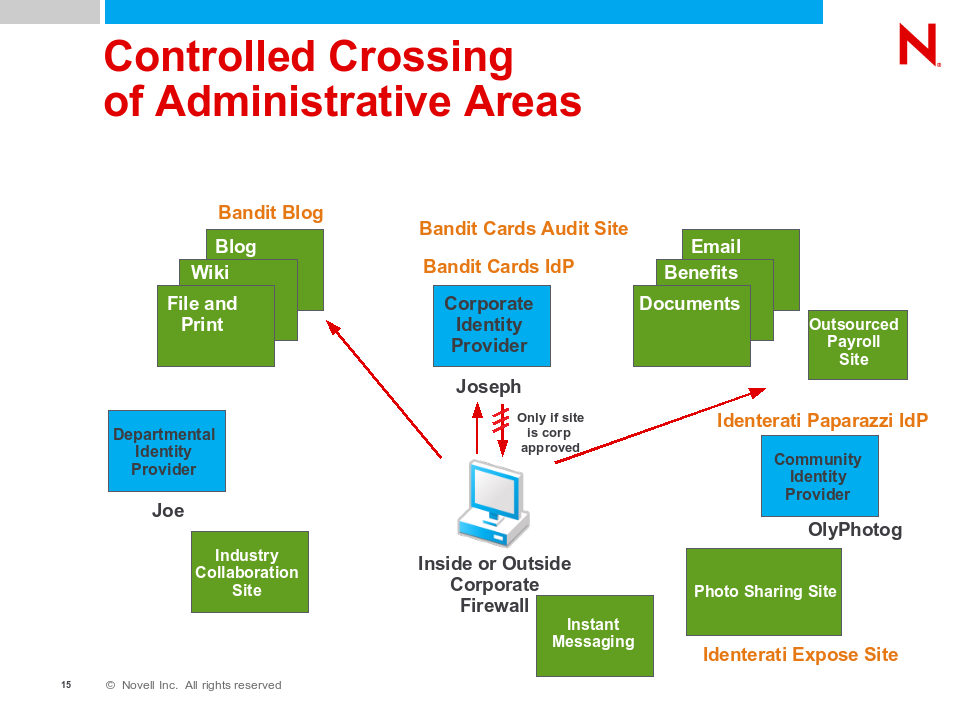
We should be able to guarantee that the Bandit Employee card could only be used at sites approved by the identity provider (Bandit Cards). The data would not be rejected by the rogue Exposé site, so if the user attempts to present their Employee card at the Exposé site, the operation must rejected at the IdP/STS. However, a Bandit Employee card should allow the user to post to the Bandit blog site. All uses of the Employee card should be audited.
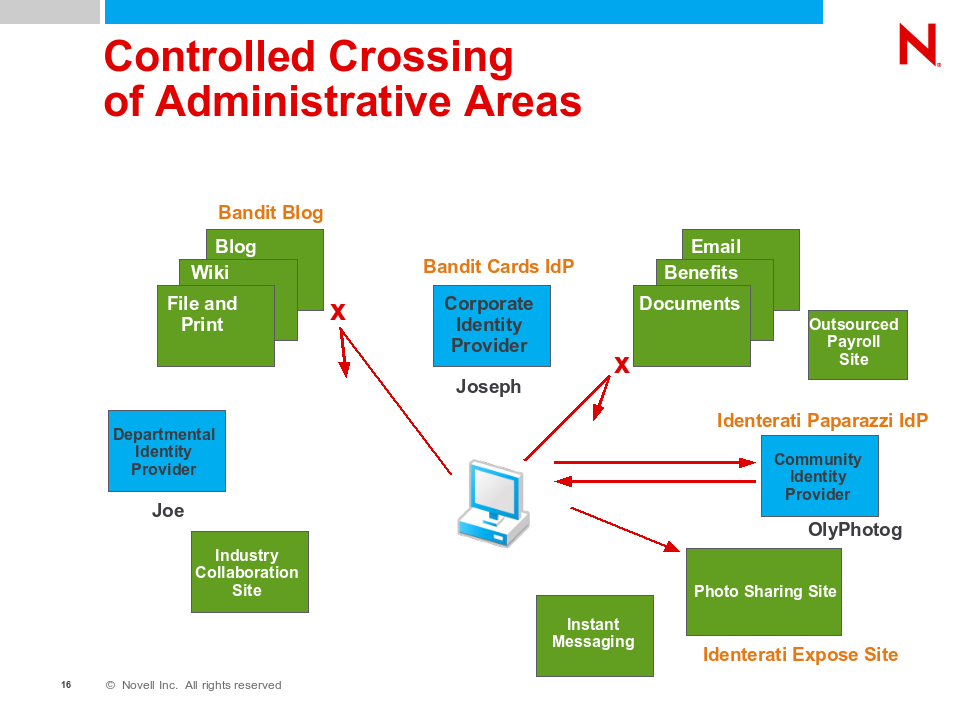
A Bandit Employee, on their own time, should be able to be a card carrying member of the Identerati Paparazzi and post photos to Identerati Exposé. Identerati Paparazzi cards should allow the user to post photos to the Identerati Exposé site, but be rejected if used to post to the Bandit Blog site.
All of these demo systems are in place and have been working in many instances for months. When you actually start using the cards as described, it’s rather intuitive.
Try it out!
Anyone can be a Bandit Employee — just create an account in Bandit Cards and issue yourself an employee card (when getting a card there is a drop-down list of card types). Unfortunately, being a self-asserted Bandit employee does not mean you get paid. Likewise you can be an Identerati Paparazzi.
So feel free to try it yourself, but please be aware that is software under active development. Some things are bound not to work. For more information or help we have mailing lists, IRC channels, bug reporting systems.
 Along those lines, at Novell’s Brainshare conference there was a panel discussion about “Open Source and User-centric Identity in the Enterprise”. The discussion was moderated by Carolyn Ford, and included Kim Cameron, Pamela Dingle, Patrick Harding, and myself. A
Along those lines, at Novell’s Brainshare conference there was a panel discussion about “Open Source and User-centric Identity in the Enterprise”. The discussion was moderated by Carolyn Ford, and included Kim Cameron, Pamela Dingle, Patrick Harding, and myself. A  For example, information card systems allow for assertions of identity data to be securely transmitted from an authoritative source to a network service in such a way that the user cannot tamper or see the data, yet is a control point for the release of the data.
For example, information card systems allow for assertions of identity data to be securely transmitted from an authoritative source to a network service in such a way that the user cannot tamper or see the data, yet is a control point for the release of the data. All of these perspectives are useful, and they are all useful within the enterprise, outside of the enterprise, and especially when crossing such boundaries.
All of these perspectives are useful, and they are all useful within the enterprise, outside of the enterprise, and especially when crossing such boundaries.
 A hub is like the proverbial silo. In the case of meta/virtual/directories the problem goes beyond the inflexibility of large identity silos like Yahoo and Google — those silos support a limited set of very tightly coupled applications. In enterprise deployments, many more applications access the same meta/virtual/directory service. As those applications come and go, new versions are added, some departments are unwilling to move, the central service must support the union of all identity data types needed by all those applications over time. It’s not whether the service can technically achieve this feat, it’s more an issue of whether the application administrators are willing to wait for delays caused by the political bottleneck that the central service inevitably becomes.
A hub is like the proverbial silo. In the case of meta/virtual/directories the problem goes beyond the inflexibility of large identity silos like Yahoo and Google — those silos support a limited set of very tightly coupled applications. In enterprise deployments, many more applications access the same meta/virtual/directory service. As those applications come and go, new versions are added, some departments are unwilling to move, the central service must support the union of all identity data types needed by all those applications over time. It’s not whether the service can technically achieve this feat, it’s more an issue of whether the application administrators are willing to wait for delays caused by the political bottleneck that the central service inevitably becomes.